Information Technology Security Management
1. IT Security Risk Management Framework, IT Security Policy, Specific management procedures and resources invested in IT Security Management:
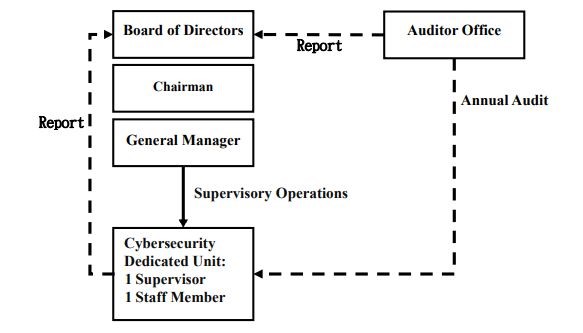
(1) IT Security Risk Management Framework The IT Security Team is responsible for coordinating and implementing IT security policies, publicizing IT security information, enhancing employees' IT security awareness, and collecting and improving technologies, products or procedures for the performance and effectiveness of the organization's IT security management system. The audit office conducts information security audits on the computer information processing cycle of the internal control procedure every year to evaluate the effectiveness of the internal control of the IT operations.
(2) IT Scurity Policy In order to implement IT Security Management, the Company has established relevant system management measures. Through the joint efforts of all colleagues, the following policy objectives are expected to be achieved.
• Ensure the confidentiality and integrity of IT assets
• Ensure that data access is regulated according to departmental functions
• Ensure the continuity of the IT systems
• Prevent unauthorized modification ou use of data and IT systems
• Perform regular IT security audits to ensure the implementation of IT security
(3) Specific Management Procedures
Internet Security Control
• Well establish the firework protection mechanism
• Regularly scan IT system and data storage for viruses
• The use of Internet services should be in line with IT security polisy
• Regularly review system log of network services to track abnormal events Data Access Control
• The IT equipments should be managed by specific personel and the system management account ID and password should be well set up and managed
• The IT systems access right should be granted based on their job functions Make sure to eliminate the access right of resigned personnels or personnel under job rotation
• Make sure to removed or overwrote those confidential, sensitive data or copyrighted software before the IT equipment is scrapped
• Application for remote access to the menagement information system should be properly reviewed and approved
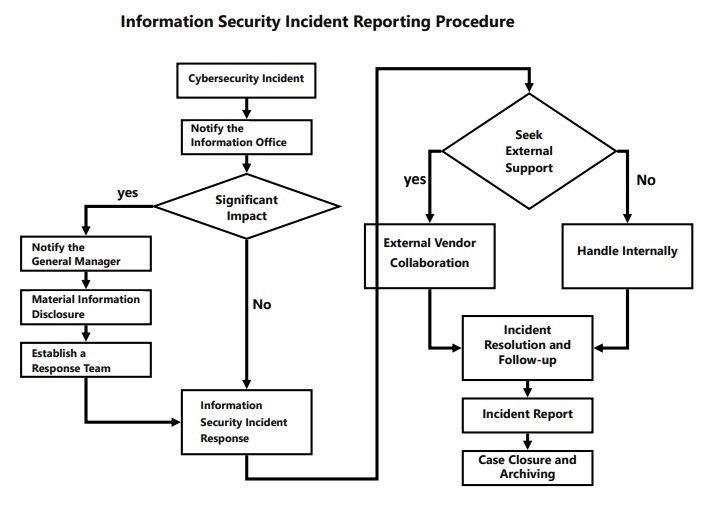
IT Contingency Plan
• Regularyly review and modify the IT Disaster Recovery Plan (DRP)
• Conduct annual disaster recovery drills according to DRP
• Establish a system backup mechanism and implement off-site backup
• Periodically review and modify network security contral measures Promotion and Inspection
• Promote IT security at any time to enhance employees’ awareness of IT seccurity
• The use of unauthorized software is strictly prohibited
(4) Resources invested in the IT safety management
• 12 hours per year of external training courses or seminars for IT security related personnel
• Advanced HiNet network protection system services
• Sophos XG125 Hardware Firewall
• Sophos Endpoint Antivirus
2. Information Technology security management operations
The IT Department regularly conducts various information security related tests and evaluations every year. In 2023, the average rate and results of various information security tests and evaluations are as follows.
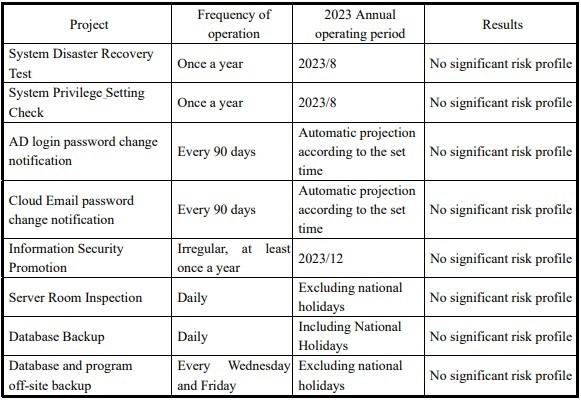
3. 2023 Data Security Performance
• There were no occurrence of material data security incidents in 2023.
• Data security audit was completed in 2023. No incompliance was found during the audit. Audit result indicates that protection capability and installation on data security are under control and complete.



